What is the Smart Contract?
Now you can listen to this article via Spotify click on the player below:
Smart contracts defined
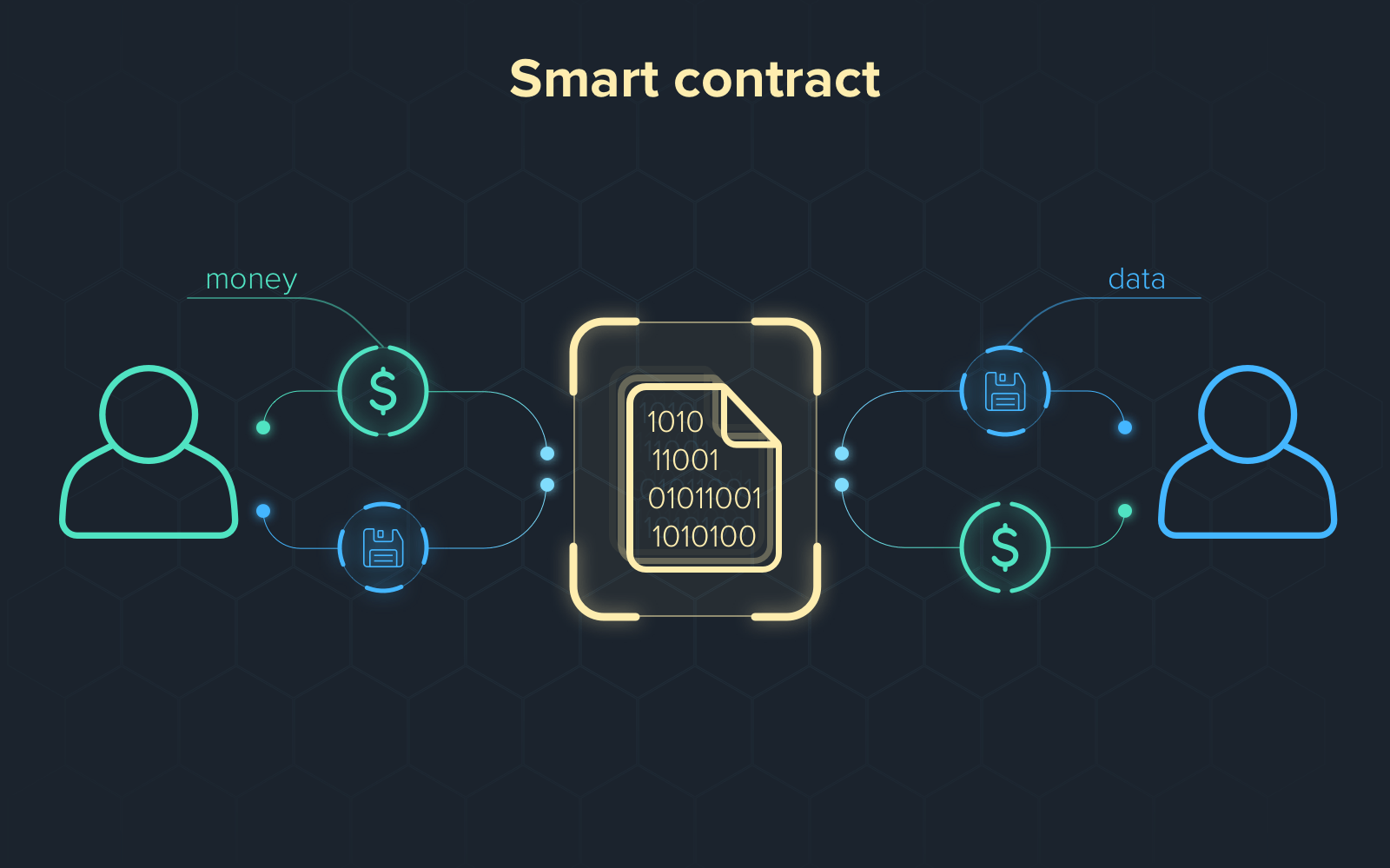
Smart contracts are simply programs stored on a blockchain that run when predetermined conditions are met. They typically are used to automate the execution of an agreement so that all participants can be immediately certain of the outcome, without an intermediary’s involvement or time loss. They can also automate a workflow, triggering the next action when conditions are met.
How smart contracts work:
Smart contracts work by following simple “if/when…then…” statements that are written into code on a blockchain. A network of computers executes the actions when predetermined conditions have been met and verified. These actions could include releasing funds to the appropriate parties, registering a vehicle, sending notifications, or issuing a ticket. The blockchain is then updated when the transaction is completed. That means the transaction cannot be changed, and only parties who have been granted permission can see the results.
Within a smart contract, there can be as many stipulations as needed to satisfy the participants that the task will be completed satisfactorily. To establish the terms, participants must determine how transactions and their data are represented on the blockchain, agree on the “if/when...then…” rules that govern those transactions, explore all possible exceptions, and define a framework for resolving disputes.
Then the smart contract can be programmed by a developer – although increasingly, organizations that use blockchain for business provide templates, web interfaces, and other online tools to simplify structuring smart contracts.
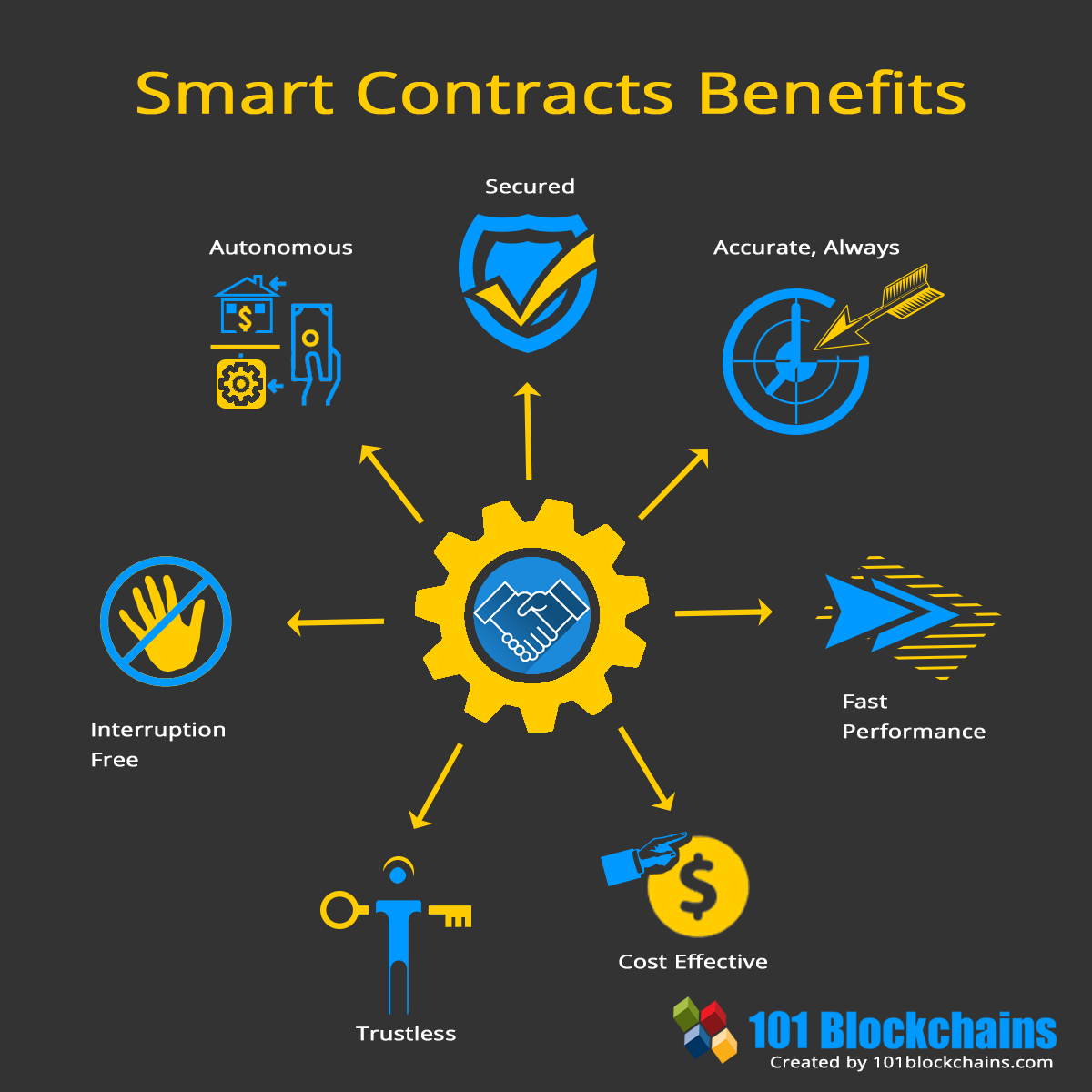
Benefits of smart contracts:
Speed, efficiency, and accuracy
Once a condition is met, the contract is executed immediately. Because smart contracts are digital and automated, there’s no paperwork to process and no time spent reconciling errors that often result from manually filling in documents.
Trust and transparency
Because there’s no third party involved, and because encrypted records of transactions are shared across participants, there’s no need to question whether information has been altered for personal benefit.
Security
Blockchain transaction records are encrypted, which makes them very hard to hack. Moreover, because each record is connected to the previous and subsequent records on a distributed ledger, hackers would have to alter the entire chain to change a single record.
Savings
Smart contracts remove the need for intermediaries to handle transactions and, by extension, their associated time delays and fees.
---------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------
Now, this article is available in audio format also:
---------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------
Follow us on Social media:
Instagram:- http://bit.ly/InstagramAudioBookMC
Deepstash:- https://deepstash.com/u/unboxingspace
Facebook page:- https://bit.ly/FacbookPageUnboxingSpace
---------------------------------------------------------------------------------------------------------------------------
Get a free e-book: https://bit.ly/Freee-BooksInPDF
---------------------------------------------------------------------------------------------------------------------------
Give your Feedback Here: http://bit.ly/FeedbackAudioBookMC
---------------------------------------------------------------------------------------------------------------------------
If you have any inquiry/ promotion ETC then e-mail 📧 us unboxingspace2020@gmail.com
The Source of information is from the "Internet & Self-analysis" ××××××××××××××××××××××××××××××××
Digital Service Provider/ Manager: https://bit.ly/InfinitygroupDM ××××××××××××××××××××××××××××××××


Comments
Post a Comment